
Private Cloud Security and Apple Intelligence: A New Era of Privacy-First AI
As artificial intelligence advances rapidly, Apple’s private cloud security is breaking ground with the June 10th introduction of Apple Intelligence. Integrated into iOS 18, iPadOS 18, and macOS Sequoia, Apple Intelligence combines cutting-edge generative models with personal context to create a more intuitive digital interaction across devices.
The cornerstone of this innovation is Private Cloud Compute (PCC), a technology that guarantees user privacy while scaling computational capacity on demand. Apple ensures personal data remains strictly confidential, unlike traditional cloud services where user data risks exposure during processing. According to Apple data “cannot be accessed in transit by anything outside those highly protected PCC nodes
What is Apple Intelligence?
Apple Intelligence represents a leap forward in personal AI technology, integrating advanced generative models with the unique personal context of each user.
By leveraging the power of Apple Silicon, including the A17 Pro and M family of chips, the AI performs complex tasks such as understanding language, creating images, and simplifying everyday activities.
Here are a few of the standout features of Apple Intelligence:
| Writing Tools: Apple Intelligence offers sophisticated writing tools that can rewrite, proofread, and summarize text across various apps, adjusting tone and style to match user preferences. | Enhanced Mail: The mail application is supercharged with Priority Messages that highlight urgent emails, smart summaries that provide concise overviews, and Smart Reply for quick responses. |
| Improved Notifications: With Priority Notifications and Reduce Interruptions Focus, users can better manage their attention and productivity. | Image Playground: This feature allows users to create custom images in Animation, Illustration, or Sketch styles, integrated seamlessly into multiple apps. |
| Genmoji: Personalized emojis can be generated based on descriptions or photos, adding a fun and unique touch to digital communication. | Advanced Photo Features: Natural language search, the Clean Up tool for removing distractions, and AI-powered Memories creation enhance photo management and editing. |
| Upgraded Siri: Siri becomes more natural, contextually aware, and capable of executing complex tasks across apps, with both voice and text input options. | ChatGPT Integration: Accessible through Siri and Writing Tools, ChatGPT integration brings advanced conversational AI capabilities with robust privacy protections. |
What is Private Cloud Compute?
Private Cloud Compute is a secure cloud intelligence system designed for private AI processing. It is the result of collaboration among Apple’s Security Engineering and Architecture (SEAR), User Privacy, Core Operating Systems (Core OS), Services Engineering (ASE), and Machine Learning and AI (AIML) teams.
The platform builds upon Apple’s longstanding commitment to user privacy, leveraging a foundation of on-device processing. This means that personal data is processed directly on the user’s device rather than being transmitted to external servers.
Apple Intelligence integrates seamlessly with PCC to enhance both privacy and computational efficiency in several key ways:
- Local Processing: Your device initially attempts to handle requests locally.
- Power Assistance: If the task requires more computational power than your device can provide, PCC steps in to assist.
- Anonymized Routing: Your queries are directed through an Oblivious HTTP relay, which conceals your IP address for anonymity.
- Selective Data Transfer: Only necessary data relevant to your task is transmitted to the PCC servers.
- Data Erasure: Once your request is fulfilled, all data, including any logs, is immediately deleted—no data retention or exposure of your identity.
This is all made possible by the integration of Apple Silicon, which provides the necessary computational power to handle complex AI tasks locally.
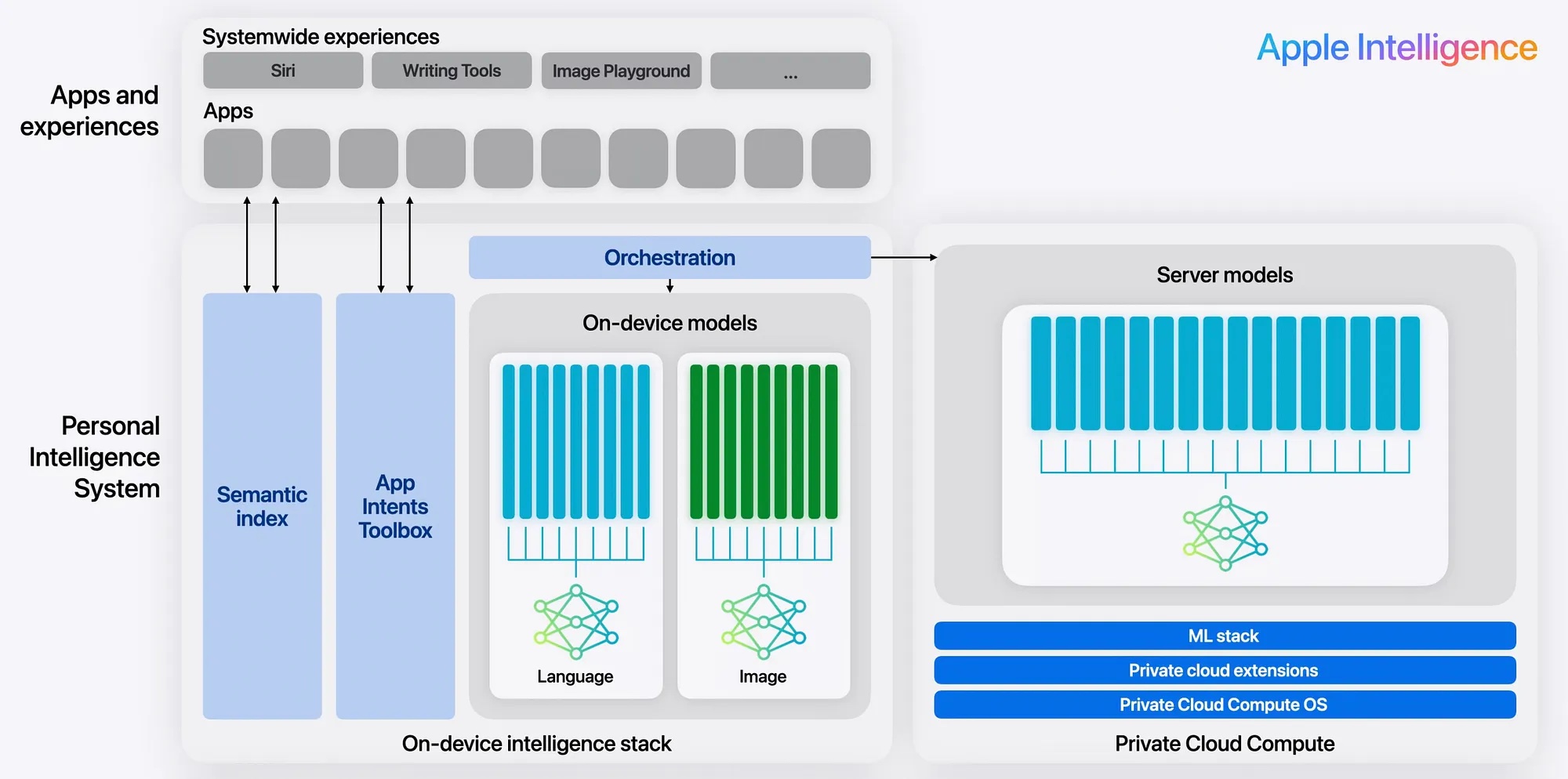
What role does Apple’s PCC play in private cloud security?
The root of trust for Apple’s private cloud security is its custom-built server hardware, which integrates the power and security of Apple Silicon with the Secure Enclave and Secure Boot (as seen in iPhones).
A specialized OS derived from iOS and macOS pairs with PCC to optimize it for Large Language Model (LLM) inference workloads, which feature a minimal attack surface.
Privacy-centric cloud extensions replace traditional data center tools, and a custom Machine Learning stack built with Swift on Server supports foundation models in a secure, controlled environment.
Let’s take a look at the requirements of PCC and the specific features developed to meet them:
Private cloud compute nodes
With end-to-end encrypted services like iMessage, operators can’t access transiting data, ensuring privacy by preventing computations on user data. However, since PCC requires access to user data for large foundation models, complete encryption isn’t feasible. Instead, PCC enforces privacy during processing and prevents data retention post-duty cycle.
Key guarantees of PCC:
- Data is used only for fulfilling requests.
- Data is deleted post-response, with no retention.
- Data is never accessible to Apple, even with administrative access.
Requests are encrypted from the user’s device to validated PCC nodes using public keys. Secure Boot and Code Signing ensure only authorized code runs. The Secure Enclave prevents key duplication and extraction. PCC nodes do not retain data across reboots due to randomized encryption keys, and memory safety techniques further enhance security.
Stateless computation and enforceable guarantees
PCC balances access to user data with robust privacy measures, as end-to-end encryption isn’t feasible due to the need for data processing by foundation models. User data is used exclusively for fulfilling inference requests and is deleted immediately afterward.
Data is encrypted end-to-end from the user’s device to PCC nodes, validated by public keys. PCC employs Secure Boot and Code Signing to make sure only authorized code runs, with Secure Enclave guaranteeing keys’ integrity and data volume encryption. Additional protections include Pointer Authentication Codes and sandboxing to thwart exploitation.
No privileged runtime access
Observability and management tools prioritize privacy, lacking general-purpose logging. Only pre-specified, audited logs can exit nodes, with multiple review layers ensuring data protection. These measures enforce that only designated code accesses user data, maintaining privacy during system administration.
Non-targetability
To thwart smaller, evasive attacks, PCC employs “target diffusion.” Metadata accompanying user requests omit personally identifiable details and includes only necessary contextual data for routing. Requests also use RSA Blind Signatures for single-use credentials, preventing association with specific users. Requests also have to pass through an external OHTTP relay that masks device IP addresses to safeguard against IP-based tracking.
Further safeguarding, user devices encrypt requests for a subset of PCC nodes selected by a blind-load balancer, which lacks user-specific data. This method ensures that compromise of a single node does not compromise all requests. Statistical auditing of node selection adds another layer of defense, deterring sophisticated attacks targeting both nodes and load balancers.
Verifiable transparency
Unlike traditional cloud services that keep their production software inaccessible to researchers, Apple plans to publish every software image used in PCC production for independent inspection. This includes operating systems, applications, and all relevant executables—available within 90 days of deployment or updates.
These images will be accompanied by cryptographically tamper-proof logs, ensuring they match precisely what’s running on PCC nodes. User devices will verify this integrity before transmitting data, using strict code signing to prevent unauthorized software. Apple will also provide a Virtual Research Environment for simulating PCC environments, release select source code subsets, and offer rewards through the Apple Security Bounty for discoveries across the entire PCC stack.
Why we’re excited about Apple’s private cloud security
At HorizonIQ, we empower you to harness the full potential of private cloud computing by using bare metal with a hypervisor of your choice. This flexibility allows you to:
- Customize your infrastructure: Choose the hypervisor that best fits your needs.
- Maintain full control: Manage the hypervisor yourself for complete oversight and adherence to your security and performance standards.
- Leverage robust infrastructure: Utilize our reliable and high-performance bare metal servers for a stable and efficient private cloud foundation.
- Scale as needed: Adjust resources based on workload demands for optimal performance and cost-efficiency.
- Ensure Compliance: Create a cloud setup that meets industry compliance standards.



