Month: July 2024

Gaming Infrastructure: How EA College Sports Football 25 Supported 700K Players
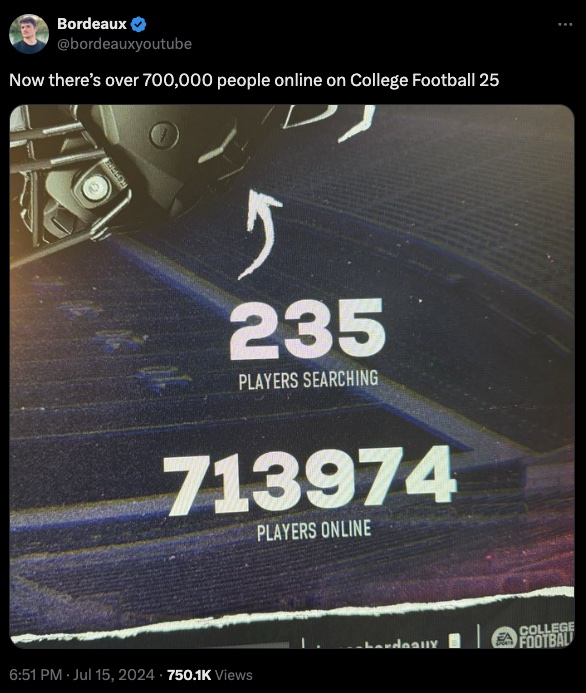
After ten years, EA Sports has brought back its college football game series with EA Sports College Football 25. The game’s launch on July 15th—for those who bought the $100 deluxe edition or used the EA Play 10-hour trial—witnessed over 700,000 concurrent players logged in across PS5 and Xbox Series X|S.
This incredible number highlights the game’s immense popularity and the critical need for latency-free gaming infrastructure. So how did EA support so many players? Let’s explore the gaming infrastructure essentials that allow for such a massive online event.
How can geographically distributed data centers provide a seamless gaming experience?
To handle the high demand, you need geographically distributed data centers to support a strong foundation. EA strategically places primary and secondary data centers in North America, South America, Africa, Europe, and Asia-Pacific to ensure the game’s core operations run smoothly.
These primary sites would be equipped with high-performance servers, capable of handling massive loads, while secondary data centers would be on standby to take over in case of failure.
But it doesn’t stop there.
To further reduce latency and improve performance, you need to deploy edge data centers in smaller, key locations. These edge centers act as local hubs, bringing the game closer to players and delivering a smooth, lag-free experience. The combination of primary, secondary, and edge data centers provides a resilient and responsive infrastructure.
What role does high-speed networking play in gaming infrastructure performance?
High-speed fiber optic connections form the backbone of gaming infrastructure, ensuring robust internet connectivity with multiple ISPs to prevent any single point of failure.
Content Delivery Networks (CDNs) like Akamai and Cloudflare play a crucial role in distributing content efficiently, reducing load times, and enhancing download speeds by caching game content closer to players.
What are the critical elements of servers and storage in gaming infrastructure?
Inside the data centers, you would need a mix of traditional physical servers and cloud-based instances to run the core game logic and databases. Virtualization with VMware and containerization with Docker and Kubernetes will optimize hardware utilization and streamline application deployment.
High-speed NVMe SSDs and centralized Storage Area Networks (SAN) will provide low-latency, high-speed data access. Meanwhile, cloud storage solutions like AWS S3 and Google Cloud Storage will securely store game assets, logs, and backups.
How do databases manage player data and game statistics?
Managing player data and game statistics requires serious database solutions. Relational databases like MySQL, PostgreSQL, and Microsoft SQL Server, both on-premises and cloud-based via Amazon RDS and Google Cloud SQL will handle structured data.
For unstructured data, NoSQL databases like Amazon DynamoDB and Google Cloud Firestore will provide fast and flexible data management.
Why are load balancers essential for managing traffic?
At the heart of managing such a large-scale online event are load balancers. Hardware load balancers from F5 and Citrix will distribute data center traffic, and virtual load balancers will manage cloud traffic.
Global load balancers will direct players to the nearest or least congested data center to optimize performance and user experience.
These load balancers ensure that no single server becomes overwhelmed by distributing the traffic load evenly across multiple servers. This not only enhances performance but also provides redundancy—if one server fails, others can take over without affecting the gaming experience.
What security tools are used to monitor and manage gaming infrastructure?
Security is crucial in any online gaming environment. Advanced firewall systems from Palo Alto will protect the network, while DDoS protection services like AWS Shield, Cloudflare, and Radware will safeguard against malicious attacks.
Encryption, both in transit and at rest, will ensure data privacy, with TLS/SSL certificates and Hardware Security Modules (HSM) managing encryption keys.
Real-time monitoring tools like Prometheus and Grafana—alongside comprehensive solutions like Datadog—will keep a vigilant eye on the infrastructure.
VMware vSphere and Kubernetes Dashboard will facilitate efficient management of virtualized and containerized environments.
In the event of catastrophic failure, backup solutions from Veeam and AWS Backup will ensure data is securely backed up, while secondary data centers and cloud-based disaster recovery services like AWS Disaster Recovery will be ready for rapid failover.
How does HorizonIQ support the gaming industry?
At HorizonIQ, we understand the latency, security, and scalability challenges the gaming industry faces. Our clients trust our bare metal servers, firewalls, and DDoS mitigation to provide the flexibility and reliability needed for their gaming infrastructures—but that’s not all.
Our engineering team recently developed new load balancers to distribute traffic intelligently across gaming environments to prevent bottlenecks, improve application availability, and enable global scalability.
With virtual and dedicated load balancers available across all our data centers, we offer flexible options to suit various needs and budgets.
Benefits of HorizonIQ Load Balancers:
- Cost-effective: Our solutions provide high performance at a lower cost compared to competitors like F5.
- Fully managed: Our experts ensure your load balancers fully optimize your infrastructure.
- Scalable and reliable: Seamless performance and minimal downtime with intelligent traffic routing.
Load Balancer options:
| Service Type | Introductory Monthly Fee |
| Virtual 200k | $99* |
| Virtual 500k | $149* |
| Dedicated 500k | $199 |
| Dedicated 1MM | $349 |
Additionally, our newly enhanced network carrier diversity with providers like Cogent Communications and Zayo Group ensures less network downtime.
Ready to elevate your gaming infrastructure:? Check out our new load balancer options.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected

Network Traffic Management: The Key to Seamless Olympic Streaming
The 2022 Beijing Winter Olympics marked a significant milestone as two billion viewers from around the world tuned in to witness the grandeur, excitement, and drama of the games in real-time. But behind this seamless experience lies a complex web of network traffic management, meticulously designed to ensure uninterrupted streaming and a superior viewer experience.
Let’s delve into how network traffic management, including load balancing and geographic distribution, played a pivotal role in delivering this monumental streaming feat.

The Network Traffic Management Challenge of Streaming the Olympics
The Olympics present unique challenges in terms of IT infrastructure due to the sheer scale of the event. With millions of concurrent viewers, varying peak times across different regions, and high-definition streaming requirements, the demand on network traffic management is immense. Ensuring that viewers enjoy a buffer-free, high-quality experience requires robust infrastructure capable of handling massive data loads and dynamic traffic patterns.
Load Balancing: The Heart of Seamless Streaming
Load balancing is a critical component in managing the heavy traffic associated with large-scale streaming events. It involves distributing incoming network traffic across multiple servers to ensure no single server becomes overwhelmed. This not only enhances performance but also improves reliability and availability.
- Traffic Distribution: By evenly distributing traffic, load balancers prevent server overloads, ensuring consistent streaming quality for all viewers.
- Failover Support: In the event of a server failure, load balancers automatically redirect traffic to healthy servers, minimizing downtime and maintaining the viewer experience.
- Scalability: Load balancing allows for the addition of servers on-demand, accommodating surges in viewership, particularly during high-profile events like the Olympics.
Geographic Distribution: Enhancing Accessibility and Redundancy
Geographic distribution of IT infrastructure is another key strategy in delivering seamless streaming experiences. By placing servers in various locations around the world, service providers can reduce latency and improve access speeds for viewers.
- Proximity to Viewers: Hosting servers closer to end-users reduces the distance data must travel, thereby decreasing latency and improving load times.
- Redundancy: Geographic diversity ensures that even if one data center experiences issues, others can pick up the slack, ensuring continuous service.
- Localized Content Delivery: With servers distributed globally, content can be cached and delivered from the nearest location, enhancing speed and reducing buffering times.
Real-Time Monitoring and Dynamic Scaling
In addition to load balancing and geographic distribution, real-time monitoring and dynamic scaling are essential for managing the complexities of streaming the Olympics.
- Real-Time Monitoring: Constant monitoring of network performance allows for immediate detection and resolution of issues, ensuring a smooth viewing experience.
- Dynamic Scaling: Automated scaling solutions can adjust resources in real-time based on traffic patterns, ensuring optimal performance regardless of viewer spikes.
HorizonIQ’s Role in Streamlining the Viewer Experience
At HorizonIQ, we specialize in providing advanced network traffic management solutions that cater to the demands of large-scale events like the Olympics. Our expertise in load balancing, geographic distribution, and real-time monitoring ensures that your content reaches viewers with minimal latency and maximum reliability.
- Comprehensive Load Balancing Solutions: Our load balancing services distribute traffic efficiently across multiple servers, ensuring high availability and performance.
- Global Server Network: With data centers strategically located around the world, we guarantee low latency and high-speed content delivery.
- 24/7 Monitoring and Support: Our team of experts provides round-the-clock monitoring and support, ready to tackle any issues that may arise.
The success of the most streamed Olympics of all time underscores the importance of network traffic management in delivering exceptional viewer experiences. Through effective load balancing, geographic distribution, and real-time monitoring, service providers can ensure uninterrupted, high-quality streaming.
At HorizonIQ, we are committed to helping you achieve these goals with our cutting-edge IT solutions. Learn how we can enhance your streaming capabilities and ensure your content reaches audiences seamlessly.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected

Data Center Disaster Recovery: Lessons from the CrowdStrike Outage
Data center disaster recovery forms the backbone of business operations, ensuring the availability and reliability of critical services is paramount. The recent CrowdStrike outage serves as a stark reminder of the vulnerabilities that can arise in even the most secure environments.
At HorizonIQ, we specialize in data center disaster recovery solutions designed to minimize downtime and maximize operational continuity. Our approach focuses on three key pillars: redundancy, geographic diversity, and carrier diversity.
The CrowdStrike Incident: A Wake-Up Call for Data Center Resilience
CrowdStrike, a renowned cybersecurity firm, recently faced a significant outage that impacted numerous services across its network. This incident highlighted how interconnected and interdependent data center infrastructures have become, making them susceptible to widespread disruptions. It also underscored the necessity for businesses to implement comprehensive disaster recovery strategies to ensure they can withstand and quickly recover from such events.
Three Key Components of Effective Data Center Disaster Recovery
Redundancy in Data Center Infrastructure
Redundancy involves having multiple, independent systems or resources in place to perform the same function, so that if one fails, others can take over seamlessly. This is critical for maintaining business continuity during unexpected disruptions.
Benefits of Data Center Redundancy
- Minimized Downtime: Redundant systems ensure that if one component fails, others can immediately pick up the slack, minimizing downtime.
- Enhanced Reliability: With redundant systems, the overall reliability of your IT infrastructure increases, providing a more stable operational environment.
- Improved Data Integrity: Redundant data storage solutions help ensure that data remains accessible and uncorrupted, even in the event of hardware failure.
Geographic Diversity in Data Center Locations
Geographic diversity involves distributing critical infrastructure components across multiple, geographically dispersed locations. This strategy helps mitigate the risk of localized disasters affecting your entire operation.
Advantages of Data Center Geographic Diversity
- Risk Mitigation: By spreading infrastructure across different regions, you reduce the likelihood of a single disaster (like a natural disaster or regional power outage) taking down all your systems.
- Load Balancing: Geographic diversity allows for better load balancing, distributing traffic and workloads across multiple locations to enhance performance and reduce bottlenecks.
- Regulatory Compliance: For businesses operating in multiple regions, geographic diversity helps meet local regulatory requirements for data storage and handling.
Carrier Diversity for Data Center Connectivity
Carrier diversity involves using multiple internet service providers (ISPs) to ensure continuous connectivity. This is crucial for maintaining access to online services and applications.
Benefits of Carrier Diversity in Data Centers
- Continuous Connectivity: If one ISP experiences an outage, traffic can be rerouted through another, ensuring uninterrupted access to critical services.
- Improved Performance: Multiple carriers can improve network performance by providing alternative routes for data traffic, reducing latency, and avoiding congestion.
- Increased Security: Carrier diversity can also enhance security by making it harder for malicious actors to target a single point of failure.
HorizonIQ’s Data Center Disaster Recovery Services
At HorizonIQ, we offer comprehensive data center disaster recovery services designed to protect your business from unexpected disruptions:
- Robust Redundancy Solutions: We implement multiple layers of redundancy across all critical systems to ensure continuous operation even in the face of component failures.
- Strategic Geographic Distribution: Our data centers are strategically located across different regions, providing geographic diversity to safeguard against localized disasters.
- Carrier Diversity: We partner with multiple ISPs to guarantee continuous connectivity, allowing your business to maintain operations and communication during outages.
Contact our sales team today to learn more about our disaster recovery solutions.
Building Resilient Data Centers with HorizonIQ
The CrowdStrike outage serves as a powerful reminder of the importance of robust data center disaster recovery strategies. By leveraging redundancy, geographic diversity, and carrier diversity, HorizonIQ helps businesses build resilient IT infrastructures capable of withstanding and quickly recovering from unexpected disruptions.
Don’t let an data center disaster cripple your operations. Invest in a comprehensive disaster recovery plan with HorizonIQ and ensure your business remains operational, no matter what.
Ready to enhance your data center disaster recovery strategy? Learn more about our services and discover how HorizonIQ can help you build a more resilient future.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected

When it comes to data storage, understanding the differences between block storage and object storage is crucial for making the right choice for your business needs.
As data continues to grow exponentially, choosing the appropriate storage solution becomes even more important. This guide will explore the key differences, benefits, and use cases of block storage vs object storage, helping you make an informed decision.

What is Block Storage?
Block storage is a method where data is divided into fixed-sized blocks, each with a unique identifier. These blocks can be stored across different environments and accessed individually. This storage type is akin to a traditional hard drive but with the flexibility of being used in cloud environments.
Key Features of Block Storage:
- High Performance: Suitable for high-performance applications such as databases and virtual machines.
- Low Latency: Offers low latency, making it ideal for transactional data.
- Flexibility: Can be used in various environments, including cloud, hybrid, and on-premises.
What is Object Storage?
Object storage, on the other hand, stores data as objects. Each object includes the data itself, metadata, and a unique identifier. Objects are stored in a flat address space, allowing for scalability and easy access over HTTP.
Key Features of Object Storage:
- Scalability: Ideal for storing large amounts of unstructured data, such as multimedia files and backups.
- Metadata Rich: Each object can have extensive metadata, providing more context and searchability.
- Cost-Effective: Typically more cost-effective for storing large volumes of data compared to block storage.
Comparing Block Storage vs Object Storage
| Category | Block Storage | Object Storage |
| Performance | Offers superior performance with low latency, making it suitable for high I/O applications. | Performance can be lower due to its structure, but it excels in storing and retrieving large volumes of data. |
| Scalability | Scalability can be challenging and might require complex configurations. | Designed for easy scalability, it can handle vast amounts of data without complex setups. |
| Data Management | Requires more management and configuration but offers greater control over data placement and performance. | Easier to manage with automated processes for handling metadata and data retrieval. |
What Are the Use Cases for Block Storage?
Databases: Block storage is perfect for database applications that require high performance and low latency. It ensures quick data access and efficient transaction processing.
Virtual Machines: Virtual machines benefit from block storage due to their ability to handle high I/O operations and provide reliable performance.
Transactional Systems: Any system that requires rapid read/write access, such as financial transaction systems, will find block storage highly effective.
What Are the Use Cases for Object Storage?
Backup and Archiving: Object storage is excellent for backup and archiving solutions, offering scalable and cost-effective storage for large volumes of data.
Multimedia Storage: Storing large files such as videos, images, and audio files is efficient with object storage due to its ability to handle unstructured data.
Big Data Analytics: For big data applications that require extensive metadata and easy access to large datasets, object storage is the preferred choice.
Why HorizonIQ
At HorizonIQ, we understand the critical role that effective storage solutions play in your business’s success. Our block storage services are designed to deliver unmatched performance, flexibility, and reliability. Here’s why HorizonIQ is the right choice for your block storage needs:
- Unmatched Performance: Our block storage solutions utilize flash-based NVMe hardware optimized for high-performance applications.
- Scalability: Easily scale your storage needs with our flexible block storage options, suitable for growing businesses.
- Reliability: With HorizonIQ, you can count on robust and reliable storage infrastructure, backed by a 100% uptime SLA for continuous availability.
- Cost-Effectiveness: Our competitive pricing ensures that you get the best value for your investment without compromising on quality.
Ready to learn more about how HorizonIQ’s block storage solutions can enhance your business operations? Explore our block storage services and discover the benefits today.
Final Considerations: Block Storage vs. Object Storage
Choosing between block storage and object storage depends on your specific business needs and use cases. While block storage offers high performance and low latency, object storage provides scalability and cost-efficiency for large volumes of unstructured data.
By understanding these differences, you can make an informed decision and select the best storage solution for your organization. HorizonIQ is here to support you with top-tier block storage solutions tailored to meet your unique requirements.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected
What are DDoS Attacks?
Websites are essential to businesses. They serve as our brand ambassadors, communication centers, and stores. However, we are also constantly exposed to a plethora of security risks because of our digital footprint, and DDoS attacks are at the top of the list.
An attack known as a DDoS (Distributed Denial-of-Service) attempts to stop legitimate users from accessing a website or server by flooding it with fraudulent traffic. A DDoS assault is essentially like trying to pass through a door on a packed street with too many people.
These assaults have the potential to be quite disruptive, leading to monetary losses, harm to one’s reputation, and irate clients. So, how do hackers carry out denial-of-service attacks, and how can you recognize and defend against these risks?
How to DDoS: A Step-By-Step Guide to Stress Testing
Step 1: Understand the Legality and Ethics
Before considering a DDoS attack, ensure you understand the legal and ethical implications:
- Legal Issues: Unauthorized attacks are illegal.
- Ethical Hacking: Use DDoS attacks only for stress testing with explicit consent and legal agreements in place.
- Consent and Control: Ensure you have the organization’s explicit consent and can control the attack to avoid real harm.
Step 2: Choose Your Method
There are several methods for stress testing, varying in complexity and impact.
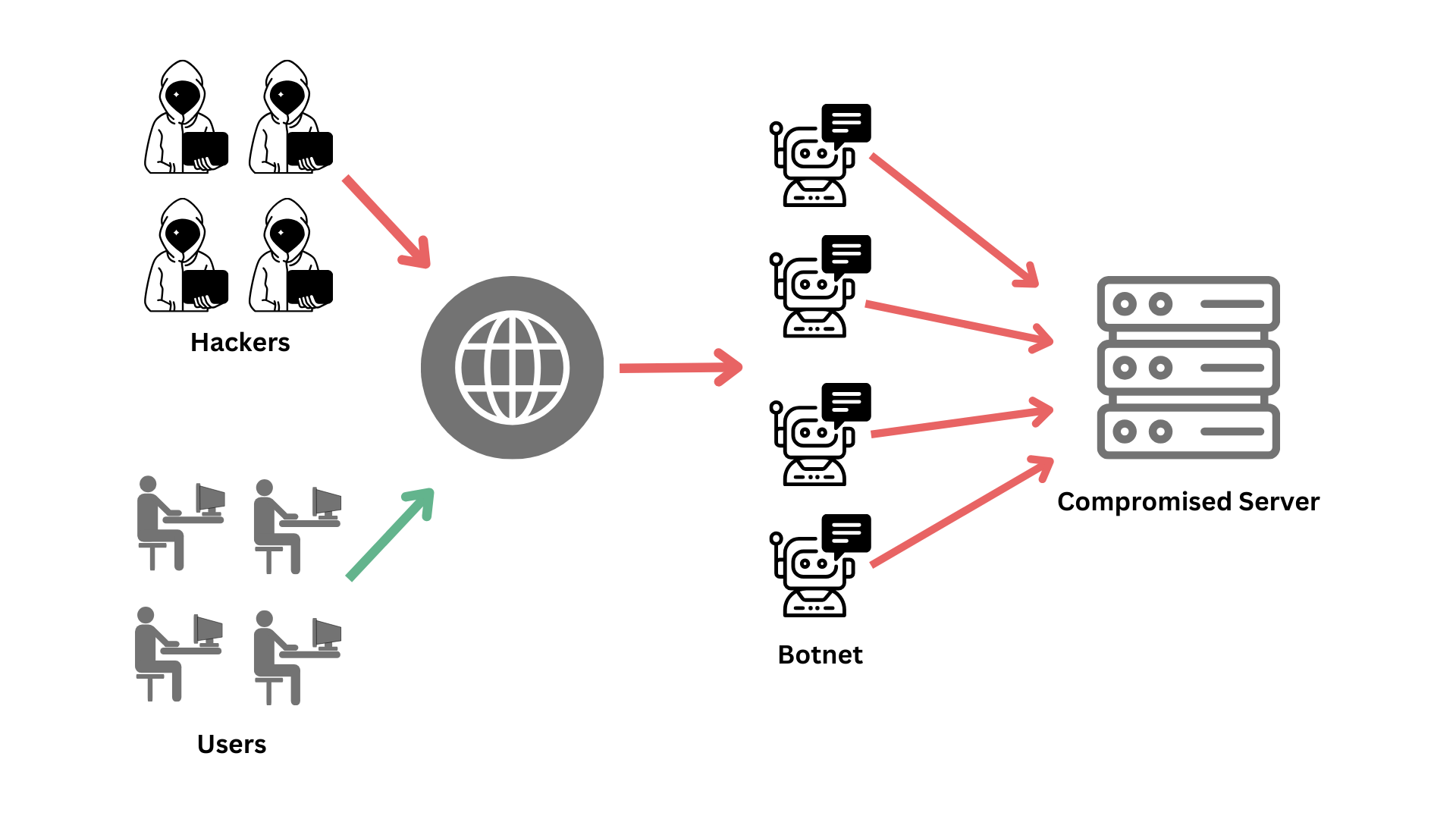
- Using Botnets:
- Definition: A botnet is a collection of compromised devices controlled by a Command-and-Control (C&C) center.
- Usage: Botnets can launch large-scale DDoS attacks by sending large amounts traffic to the target.
- Availability: Some botnets are available for rent, often used for illegal activities such as spam, phishing, or cryptocurrency mining.
- Using DDoS Programs and Tools:
- Individual Efforts: Small-scale hackers without botnet access use specialized tools to direct traffic from their computers.
- Crowdsourcing: Gathers multiple users to download and use tools simultaneously, increasing the attack’s impact.
- Tools List:
- HULK (HTTP Unbearable Load King)
- XOIC
- R-U-Dead-Yet
- Low Orbit Ion Cannon (LOIC)
- Tor’s Hammer
- DDOSIM – Layer 7 DDoS Simulator
Step 3: Establishing a Botnet
If using a botnet, the following steps are typically involved:
- Infect Devices: Spread malware to compromise a network of devices, creating a botnet. This includes computers and IoT devices.
- Control the Botnet: Use a Command-and-Control center to manage the infected devices.
- Send Commands: Direct the botnet to send requests to the target’s IP address, overwhelming the server or network.
Step 4: Launching the Attack
Whether using a botnet or DDoS tools, follow these steps to launch the attack:
- Preparation: Ensure all tools, devices, and personnel are ready.
- Coordination: If crowdsourcing, coordinate with participants to launch the attack simultaneously.
- Execution: Direct the traffic to the target’s IP address.
- Monitoring: Carefully monitor the attack to control its impact and avoid causing unintended damage.
How Can I Spot a DDoS Attack?
DDoS attacks can manifest in various ways, but some common signs include:
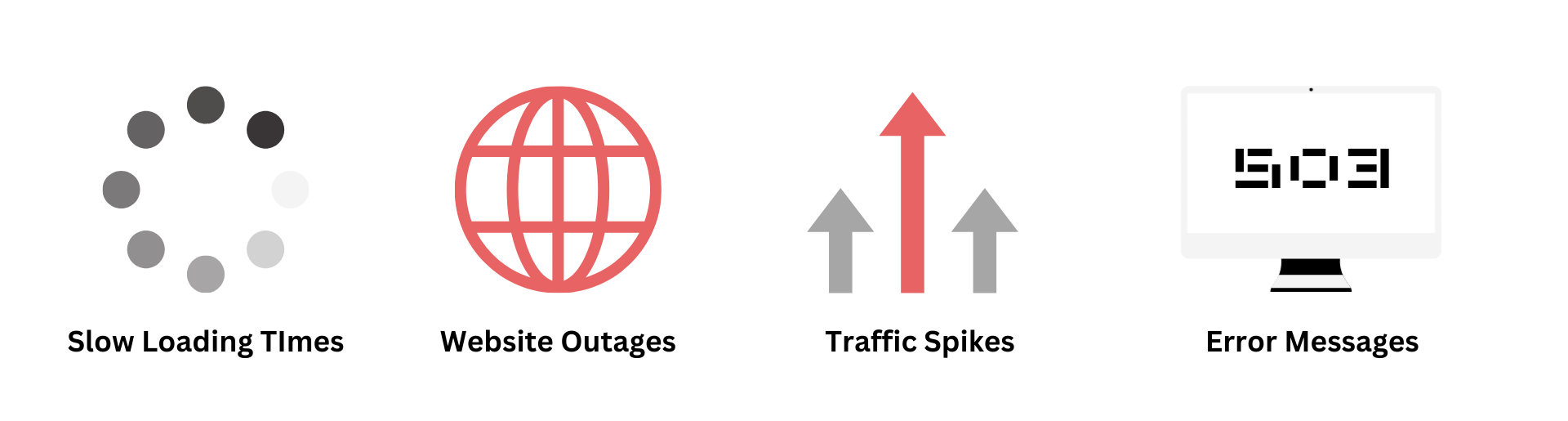
| Sign | Description |
Slow website loading times |
This indicates that your server is struggling to handle an unusually high volume of traffic. |
Complete website outages |
If your website becomes entirely inaccessible, a DDoS attack could be the culprit. |
Unusual traffic patterns |
Spikes in Google Analytics traffic from unexpected locations or a single source can be red flags. |
Error messages |
Server overload errors often accompany DDoS attacks. |
Pro tip: If you experience any combination of these signs, staying calm and alerting your engineering team to take immediate action is crucial.
How Can I Build a Stronger Defense to Mitigate Attacks?
There are strategies to combat DDoS attacks. Here are some key steps to consider:
| Strategy | Description |
Utilize a DDoS mitigation service |
Partnering with a reliable security provider like HorizonIQ provides a defense system that filters out malicious traffic before it reaches your servers, keeping your website operational. |
Implement rate limiting |
Restricts the number of requests a single IP address can send to your server within a specific timeframe, preventing a flood of traffic from a single source. |
Regularly update software |
Keeping software up-to-date with the latest patches reduces vulnerabilities that attackers may exploit. |
Educate employees on DDoS attacks |
Training employees on cyber security best practices can help them recognize phishing attempts and reduce the risk of DDoS attacks. |
Why Should I Choose HorizonIQ for DDoS Mitigation?
At HorizonIQ, we know how vital your website is to the success of your company. That is why we provide a full range of DDoS protection services at our Secaucus, Amsterdam, Chicago, and Phoenix data centers to safeguard your online presence.
What distinguishes us?
- Advanced threat detection: We can minimize disruptions by using our state-of-the-art technology to quickly identify and filter out unwanted communications.
- Global network infrastructure: We can efficiently absorb and mitigate DDoS attacks from any location in the world thanks to our carefully positioned data centers.
- Expertise in security available around the clock: We have seasoned security specialists on hand to keep an eye on your network and proactively counter attacks.
Don’t let a DDoS attack cripple your business. By understanding DDoS attacks, implementing mitigation strategies, and partnering with a trusted provider like HorizonIQ, you can build a robust defense protected from fast-moving, high-volume, encrypted, or very short-duration threats.
Contact us today and explore our best-in-class DDoS protection solutions.
Please note: While HorizonIQ offers a variety of security solutions globally, DDoS mitigation is currently available at our data centers in Amsterdam, Chicago, Phoenix, and Secaucus.