Month: April 2020

MDR Requires Visibility and Vigilance
Today we are pleased to welcome guest blogger Tony Bradley, Senior Manager of Content Marketing for Alert Logic, INAP’s trusted managed security partner and expert in cloud security for financial services customers.
– Wendy Williams, Product Manager, INAP
In an increasingly complex business environment, cybersecurity challenges have become more urgent as organizations accelerate their digital transformation. Rapid changes in technology and an ever-expanding threat landscape add extra strain to businesses that are already challenged to focus on productivity and customer needs. Working with a managed detection and response (MDR) provider is an effective way to address cybersecurity, but there is confusion about the value that MDR delivers, and the capabilities that solid MDR requires. Most importantly, effective MDR requires comprehensive visibility and 24/7 monitoring.
No matter how large or small an organization is, where it’s located, or what industry it is in, there are some simple truths when it comes to cybersecurity: You can’t protect assets you’re not even aware of, and you can’t do security part-time.
Comprehensive Visibility
Most attacks are not targeted efforts to specifically compromise a given company or network. They use automated utilities that can identify, and then exploit, vulnerable platforms and services. It’s the same with attacks against end users, where many of the most successful malware campaigns are highly automated, even where social engineering is involved. As a result, most systems and users are always potential targets, illustrating the need for insight.
Even with the right preventative tools and processes in place, organizations are still vulnerable without comprehensive visibility. No CIO or security team will ever assert that they are 100 percent secure, and activities like vulnerability scans, timely patching and network monitoring are great, but it will be the systems you don’t patch or monitor that become your Achilles’ heel. Without a holistic view of the environment, there are likely devices on your network with open ports or critical vulnerabilities waiting to be discovered and exploited by attackers. Even if everything is locked tight today, without full visibility, that level of protection can change quickly—and without warning—if there are configuration errors or new vulnerabilities discovered in deployed software.
When partnering with an outside vendor for security, it is important that the vendor has an understanding of your environment and your business objectives to ensure they understand the scope and context of an event. They must be able to identify new systems, detect vulnerabilities and inform your patching strategy and security best practices to protect you.
Constant Vigilance
Another crucial capability of effective MDR is 24/7 monitoring. Comprehensive visibility is imperative, but attackers don’t keep office hours. Cyber attackers live and operate around the world—when it’s 3 a.m. for you, it’s 1 p.m. somewhere else. Equally important, as mentioned above, most campaigns and tools are automated and executing around the clock.
Sophisticated attacks do not occur as simple moment-in-time events, either. A campaign or exploit can be triggered at any time, and different elements of a complex campaign may execute at delayed time intervals designed to evade triggering alerts and avoid detection. Effective managed detection and response requires 24/7 effort to gather and analyze intelligence and expert insight from security professionals to continuously monitor the environment and ensure quick response to suspicious activity and security incidents.
Learn More
On May 5, Jack Danahy, Chief Evangelist for Alert Logic, Jennifer Curry, Senior Vice President, Global Cloud Services for INAP, and Fran Howarth, Practice Leader, Security for Bloor Research participated in a webcast titled, “Are You Providing Always-on, Pervasive Coverage and Visibility to Keep Your Entire Infrastructure Environment Safe and Secure?”
Click here to watch the webcast replay.

About the Author
Tony Bradley is Senior Manager of Content Marketing for Alert Logic. Tony worked in the trenches as a network administrator and security consultant before shifting to the marketing and writing side of things. He is an 11-time Microsoft MVP in security and cloud and has been a CISSP-ISSAP since 2002. Tony has authored or co-authored a dozen books on IT and IT security topics, and is a prolific contributor to online media sites such as Forbes and DevOps.com.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected
Connecting Our ‘Inner Networks’ Through Yoga, Powered by INAP
As the new reality of the work from home lifestyle began to sink in, we at INAP started looking for new ways to connect with our employees, partners and clients. Enter INAP Marketing Specialist Nicolette Downs. As a yoga instructor and owner of Chicago’s own Big Shoulders Yoga Studio, she’s graciously stepped onto her mat to offer twice-weekly yoga classes via Instagram Live.
“The virtual INAP yoga classes are a great break in the day and have helped with my flexibility and focus,” said Matt Cutler, National Account Manager.
You can join Downs and other members of the INAP family on Tuesdays and Thursdays at 12 p.m. Eastern Time. All you have to do is follow us @poweredbyinap on Instagram and you can join the free classes in real time or watch them on our Instagram story for up to 24 hours after the live class. The 30-minute classes are the perfect way to take a short break, connect with others, reconnect with yourself and get your body moving.
“It’s great to take 30 minutes in the middle of the day to step away from my desk and move my body,” said Kandace Hyland, Senior Marketing Manager. “I come back re-energized to do whatever project I’m working on that day.”
Attending live classes can also bring some much needed routine to your day, as Human Resources Generalist Anastacia Cesario can attest. “Taking live classes during this quarantine helps me feel like there is some sort of normality in my day still and helps me stick to a schedule.”
Yogis of all levels can participate, whether you’re a seasoned expert or have never taken a yoga class in your life.
National Account Manager Joseph Shaughnessy has been able to find a new challenge and goal to strive for through these classes. “I’m still trying to perfect my ‘crow pose,’” he said. “A lot of practice is needed!”
You won’t need any special equipment to participate. If you don’t have access to a mat, a towel or blanket can serve as a stand-in. Downs often offers up substitutes for the typical props used in the yoga studio at the beginning of the live broadcast and throughout the practice.
We hope we’re able to provide the small break you need in your day to keep you feeling grounded as we make our way through these unprecedented times. And as always, we’re here to help you find the solutions you need to maintain your connectivity, whether it be through yoga to keep you up and running, or an IT solution to keep your business going.
Know Your Yoga Moves
New to yoga and want to be better prepared? There are many poses to explore in class that aren’t covered below, including crow pose, which Shaughnessy mentioned he’s working on and is a pose that allows you to get some “network uptime.” But the poses that follow are some of the moves you’ll frequently see in our classes.
Downs also provides modifications during the class in order to help accommodate limitations.
Backbone Connection Pose (Downward Dog)

This is a common pose across all styles of yoga. This spine-lengthening pose will help you shake off long days sitting in front of a computer.
From all fours, ground your hands into the mat, putting the weight into your thumbs and forefingers to take any strain off of your wrists. Lift your hips and bend your knees, coming onto the balls of your feet. Bring your shins parallel to the mat and keep your sit bones lifting high and back and you straighten your legs. Once in position, you can peddle out your feet as you work to melt your heels toward the floor.
Hyper-V (Boat Pose)

This pose will really rev up your core. You’ll begin seated with your knees bent and feet flat on the mat. Lean back slightly and lift your legs to bring your shins parallel to the floor. Maintain tension in your core to ensure that your spine doesn’t round down. We want a nice straight back and a lifted chest in this pose.
As you maintain the balance on your sit bones, straighten your legs to your comfort level. In the photo above, Downs in demonstrating the maximum extension. Lift your arms and reach forward, keeping your arms and hands actively engaged. We’ll typically draw several rounds of breath in this pose.
To release, exhale as you lower your legs and hands to the floor.
Network Branch Pose (Tree Pose)

Challenge your balance! Throughout this balance pose, keep your gaze fixed on an unmoving point in front of you. Begin by standing on your mat with your arms at your side. For this example, we’ll pretend you’re starting with the balance on your left leg. Shift your weight to your left foot and bend your right knee.
Lift your right leg or use your hand to draw your right foot alongside your inner left thigh, your left calf or your left ankle, depending on your flexibility level. To protect your knee, do not rest your foot against the knee joint.
Place your hands on your hips and lengthen your tailbone toward the floor. Then, press your palms together in a prayer position at your chest, with your thumbs resting on your sternum. You can stay in this position, or take the balance a step further by reaching your network branches up overhead.
Web Firewall Application Pose (Warrior II)

This pose will give your quad muscles a run for their money. Step your feet apart, using your mat or towel as a guide. Raise your arms parallel, palms facing down, and reach them actively out to the sides. Keep the front foot pointed forward and turn your back foot out. The front and back heels should be aligned as the feet run perpendicular to each other.
Bend your left knee over the left ankle, so that the shin is perpendicular to the floor. This is where you’ll feel the quad go to work. Anchor this movement of the front knee by strengthening the back leg as you press the outer back heel firmly to the floor. Turn you head forward to look out over your fingers.
Concluding the Practice

Each practice concludes with savasana, or what we’re calling NAP Pose. You’ll get a chance to lie back on the mat, relax and thank yourself for the work you just did. Then, after that final relaxation, we seal the practice by sitting cross legged and saying, “Namaste,” which roughly means, “The light within me honors and respects the light within you.”
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected

IT Pros Pick the Household Pets Most Representative of Their Work Styles in New INAP Survey
Millions of us who have shifted to work from home situations during this challenging time find ourselves adjusting to new “coworkers”—some of whom are of the four-legged variety. Are the personalities of your new office colleagues affecting your work style? Do your pets remind you of any of your actual coworkers?
It just so happens that INAP polled 500 IT pros to determine which household pets best replicate their on-the-job personas. Respondents were asked to choose their primary from a list of household and exotic pets and corresponding characteristics. Since most people don’t fit perfectly in a box, participants were given the option to select a secondary persona, as well. The results aren’t very scientific but are revealing, nevertheless.
Pet Personality Types
It’s easy for those outside of IT to lump the entire profession into one persona. Pop culture tropes are likely to blame. (Thanks, Jimmy Fallon.) But we know, like any discipline, there’s a spectrum.
Have you ever met a sysadmin whose go-it-alone attitude is suspiciously cat-like? Or a network engineer who is as loyal and enthusiastic as a golden retriever? How about a hot-aisle-loving D.C. tech who can camouflage their emotions with iguana-like deflection?
Check out the descriptions for the eight pets featured in the survey below and consider where you and your coworkers might fall.
-

Dogs
IT dogs always appear happy. They thrive off positive feedback and incentives. They are loyal, but oftentimes to a fault.
-

Cats
IT cats need little direction and prefer to work independently. They often come across as aloof or standoffish, despite a hidden soft side.
-

IGUANAS
IT iguanas are experts at adapting to whatever the work environment throws at them. However, they often camouflage their true opinions during conflict, making them tough to pin down.
-
Fish
IT fish are experts at swimming through the backlog. However, they tend to always sleep with their eyes open in anticipation of the next problem at work.
-

TARANTULAS
IT tarantulas, with eyes on everything, never miss a chance to seize an opportunity at work. They are respected, but often intimidate colleagues and subordinates.
-

PARROTS
IT parrots are highly intelligent and absorb knowledge fast. But they’re also commonly viewed as arrogant and are prone to occasionally sh***ing all over colleagues.
-
TURTLES
IT turtles work slow and steady, but often get the job done better than anyone at the office. However, they would rather hide in their shell than engage in a workplace conflict.
-

HEDGEHOGS
IT hedgehogs work diligently through the night. However, they can become reclusive and prickly if not managed to their liking.
Results: Pet Personas in the Workplace
The IT pros participating in the survey reviewed the choices and selected their primary and secondary pet personality types.
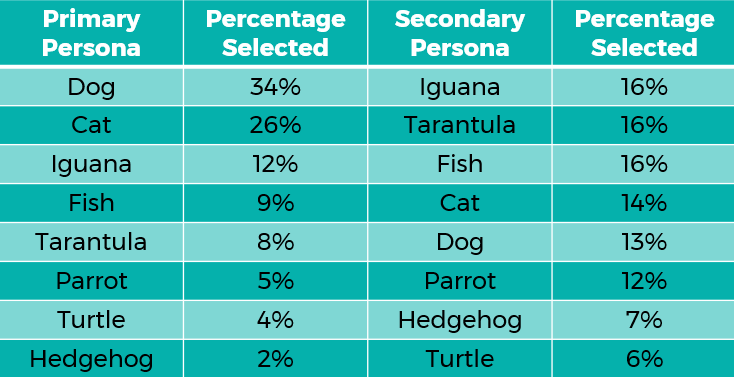
Dog took the No. 1 spot, with 34 percent of survey takers choosing it as their primary persona. In fact, 31 pros selected this as their only pet persona. Interestingly, senior IT leaders are 17 percent more likely to be dogs than non-senior leaders. Perhaps that loyal streak took them a long way.
Optimism also abounds with these IT pros. IT Dogs are 41 percent more likely than IT Cats to think their infrastructure strategy deserves an “A” grade.
Cat finished second, with 26 percent of IT pros selecting it as a primary persona. With an ability to work independently with little direction, 14 percent of respondents selected cat as their secondary persona, a statistic that might be heartening to managers.
With dogs and cats ranking as the No. 1 and No. 2 “most popular pets in America,” it shouldn’t be surprising that we identify their traits in ourselves.
Iguana took the No. 3 spot, with 12 percent of IT professionals identifying with the ability to adapt to whatever their work environments throw at them. That’s a terrific trait to have in an ever-shifting tech landscape where it’s challenging to predict what might come next.
IT iguanas tied for the most common secondary persona, with 16 percent of respondents selecting it. Interestingly, non-senior IT leaders are 70 percent more likely to be Iguana primaries than senior leaders.
Fish claimed the No. 4 spot overall, with 9 percent of IT professionals selecting it as their primary persona. And as a secondary persona, fish tied for No. 1 with 16 percent. It was also the most common secondary persona for non-senior IT infrastructure pros. This is good news, as the field needs pros who are experts at swimming through the backlog in order to move forward.
At No. 5 overall, tarantula was selected as a primary persona by 8 percent of IT pros, and it tied with fish for the No. 1 spot as a secondary persona. With eyes on everything, ready to seize opportunities, Senior IT leaders are twice as likely to be tarantulas than non-senior leaders.
Parrot claimed the No. 6 spot, with 5 percent of IT pros willing to admit that, at times, and despite their high intelligence, they can have a tendency to s**t all over their colleagues. That’s some high-level introspection and honesty in our book. As secondary personas go, 12 percent of survey takers selected parrot. Parrots are equally likely to be leaders as non-leaders.
Known for quality work output at a slow and steady pace, turtle was selected as a primary persona by 4 percent of IT professionals, bringing it to the No. 7 spot. Only 6 percent selected turtle as their secondary persona, which ranks 8 out of 8. Interestingly, non-senior leaders were twice as likely to be turtles as non-senior leaders, which begs the question: Is conflict required to lead? Based on these survey results, it seems likely.
And finally, hedgehog secured the last spot, at No. 8, with 2 percent of IT professionals selecting it as their primary persona. Hedgehog came in 7 out of 8 for secondary personas. These IT third-shifters work diligently through the night.
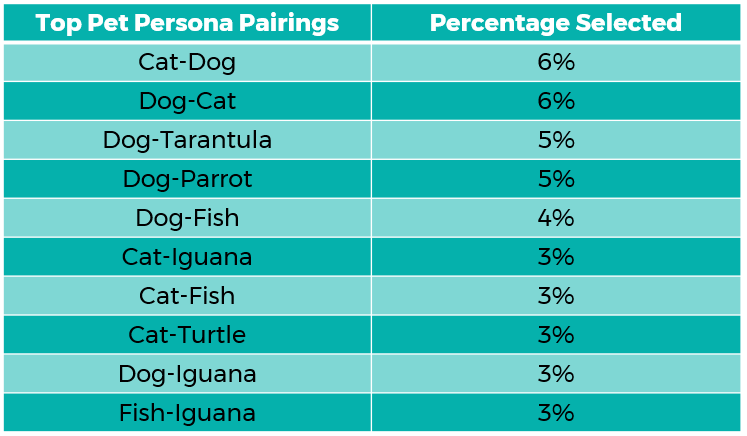
Top Animal Persona Pairings
Below is a breakdown of the top pet persona pairings across the entire sample. The primary persona is listed first in each pairing.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected

Cyberattacks have been plaguing the top headlines for years and security continues to be a top priority for enterprises across the globe. In fact, when IT pros were asked their top challenges for 2020, protecting their organizations from cyberattacks came in second only to migrating applications to the cloud.
Many of these pros also noted that cybersecurity would have been a good area to focus on had they known when they entered the field how important security would become. And this is not without reason. Criminals perpetrating cyberattacks keep shifting their strategies to expose new vulnerabilities, and cybersecurity experts are essential to stop these attackers in their tracks.
As the cybersecurity landscape continues to evolve, it’s crucial to maintain awareness and adjust security strategies accordingly. Let’s explore what’s changing and which attacks are on the rise.
Targeted Ransomware Attacks
Public reports from various vendors such as Check Point, Verisign and others all seem to agree that mass ransomware attacks peaked in 2017 and ran through 2018, with 30 percent of businesses and home users affected, according to Checkpoint’s 2020 Cyber Security Report. But a peak doesn’t mean that ransomware attacks are going away, rather, they shifted to more targeted ransomware attacks in 2019.
Alert Logic notes in their Critical Watch Report that ransomware continues to be a popular cyberattack due to its profitability, simplicity (because it can be conducted from a computer anywhere in the world) and anonymity. Malicious attackers are always adapting to new environments and IT protection strategies. The larger numbers of attacks in 2017 were reported from organizations that received phishing emails containing ransomware software. This technique has a fairly low success rate. With the end goal of a company paying an attacker for encryption keys, there is also low probability that the majority of these organizations would even have the available funds to pay in the first place. A more targeted and sophisticated effort proves to have a much higher success rate.
Rising Popularity of Cryptojacking
With ransomware attacks on the decline, cryptojacking—a type of cyberattack in which a hacker secretly uses a target’s computer to mine for cryptocurrency—is seeing a massive rise in popularity. It’s less visible and doesn’t require the same effort as ransomware. One of the many examples of this trend is a cryptojacking attack on a cloud mining service, which took the scripting service offline for weeks and resulted in 65-million-dollars in stolen cryptocurrency. While the company was able to recover most of the currency, cryptojacking attacks continue to deliver potentially business-ending consequences to vulnerable organizations.
Attackers are evolving to use many of the same exploit measures that spammers and DDoS attackers have been using for years. Gaining control of a machine through known vulnerabilities and using those compromised machines idles computing cycles to join a mining pool.
There were 52.7 million cryptojacking hits in the first half of 2019. Cryptojacking is a growing threat as we progress into 2020, and we can expect that more and more idle compute resources will be compromised.
Evolving DDoS Attacks
DDoS attacks are still a rising method of cyberattack, and just like ransomware attacks morphing into cryptojacking, DDoS attacks are also evolving.
Neustar’s Q2 and Q3 2019 reports suggest that the attack intensity, measured in Mpps (million packets per second), as well as attack size, measured in Gbps (gigabits per second), is dropping. The average intensity of attacks in 2018 measured at 4.5 Mpps, while the average was 1.3 Mpps. The largest DDoS attack, recorded in 2018, registered at 1.7 Tbps. The average attack size in 2019 was around 7.5 Gbps. This suggests that DDoS attacks are currently undergoing the same process of refinement as ransomware attacks.
Increasingly sophisticated DDoS attacks are being used not to take a whole service offline with a volumetric attack, but to strategically target specific ports, gateways, services or applications. These attacks require much less traffic to take a service offline, and many times the attack is focused on network degradation as opposed to a downed site event.
Other Types of Cyberattacks
While some of these more popular attacks types peaked from 2017 and 2018, a few new forms of attacks are on the rise. Some are using classic tactics, with malicious attackers going back to more simplistic attack styles to exploit areas that may be lightly secured by more corporations. Attacks using web-form hijacking techniques are on the rise, and while it seems as though most companies have adequate controls, JavaScript-based attacks served 16 percent of all global attacks for the first half of 2019.
JavaScript based attacks are reported only third to EXE and DOC based attacks. While many organizations have defense software or hardware to protect their services on an application level, there may still be gaps in security that allow for vulnerabilities. A failed policy to delete an administrator account after an employee departure, a patch that was never applied to an application or crucial upgrades to software that can’t be implemented due to how the application is developed all can result in an attack.
Preventing Vulnerabilities
In 2020, it’s more crucial than ever to update both business and technical security policies. Finding a partner you can trust is an important first step to effectively getting ahead of these evolving attacks, and to navigating and managing the complex tools that will keep your organization safe.
At INAP, we offer managed security services for all cloud products that extend your team and safeguard critical infrastructure. Do your homework to ensure whichever partner you choose can adequately safeguard your infrastructure solutions, as well as adequately address the evolving cyberattack landscape.